DNS over anything, encrypted
Carsten Strotmann
Created: 2017-08-26 Sa 06:18
DNS Privacy
DNS is metadata
- IETF started the DPRIVE (DNS Privacy Working Group) after the Snowden revelations
- RFC 7672 DNS Privacy Considerations
- current focus of DPRIVE is the client to resolver channel
- creating protocols that are stealthy sometimes painfully collides with clean protocol design
QNAME Minimization
- DNS protocol has been implemented quite "chatty"
- not required by the DNS protocol
- RFC 7816 DNS Query Name Minimisation to Improve Privacy
original DNS queries 1/6
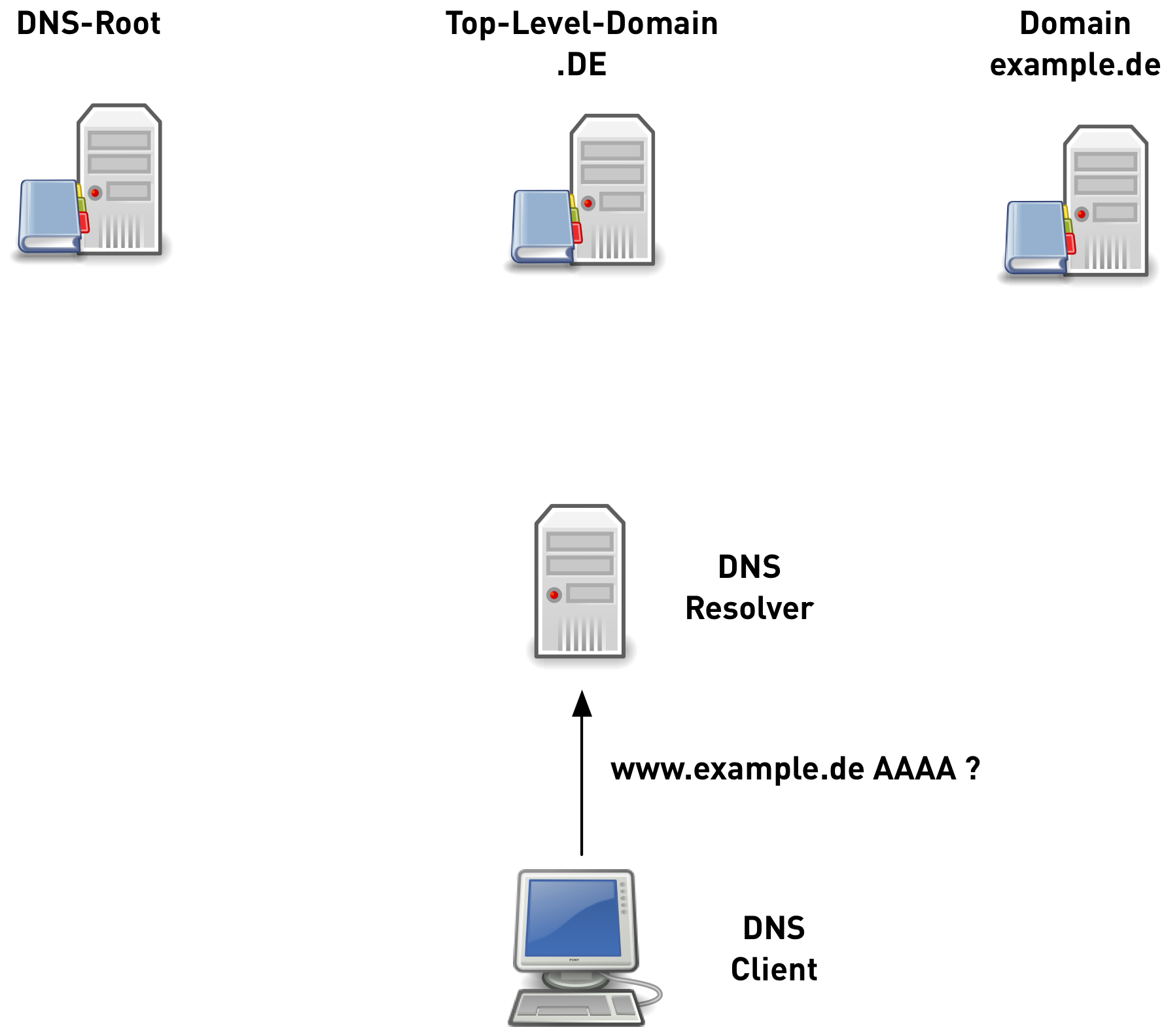
original DNS queries 2/6
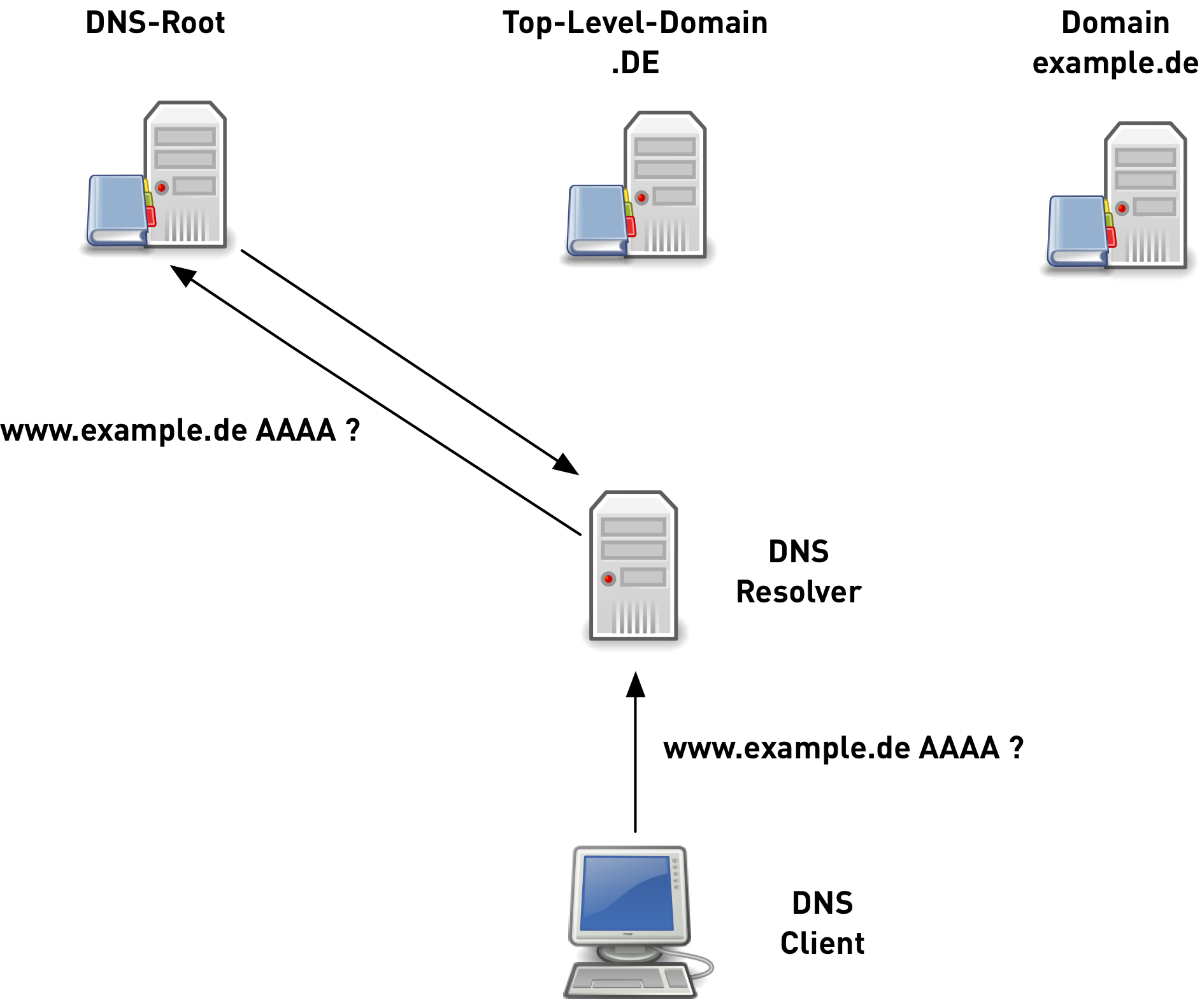
original DNS queries 3/6
original DNS queries 4/6
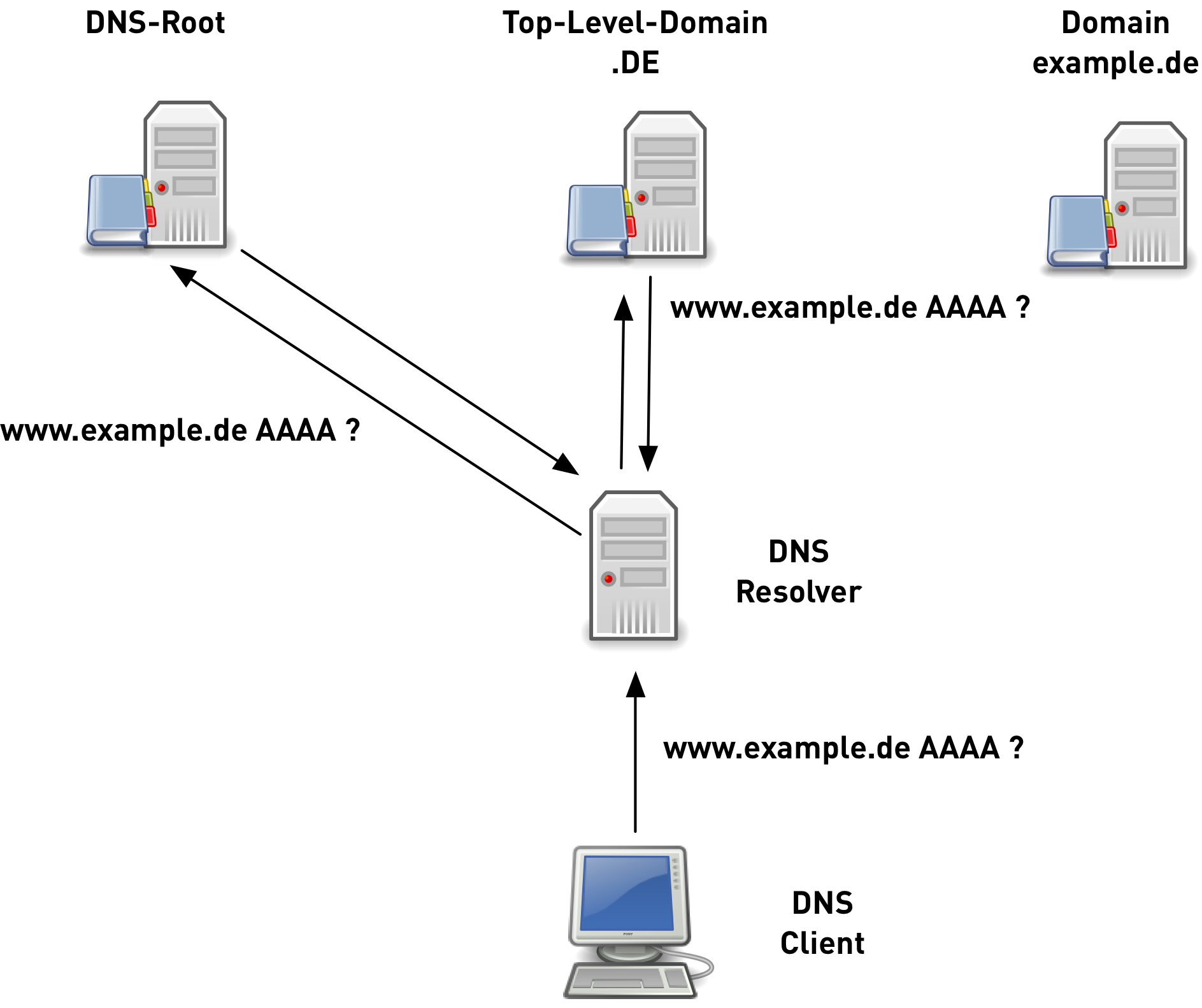
original DNS queries 5/6
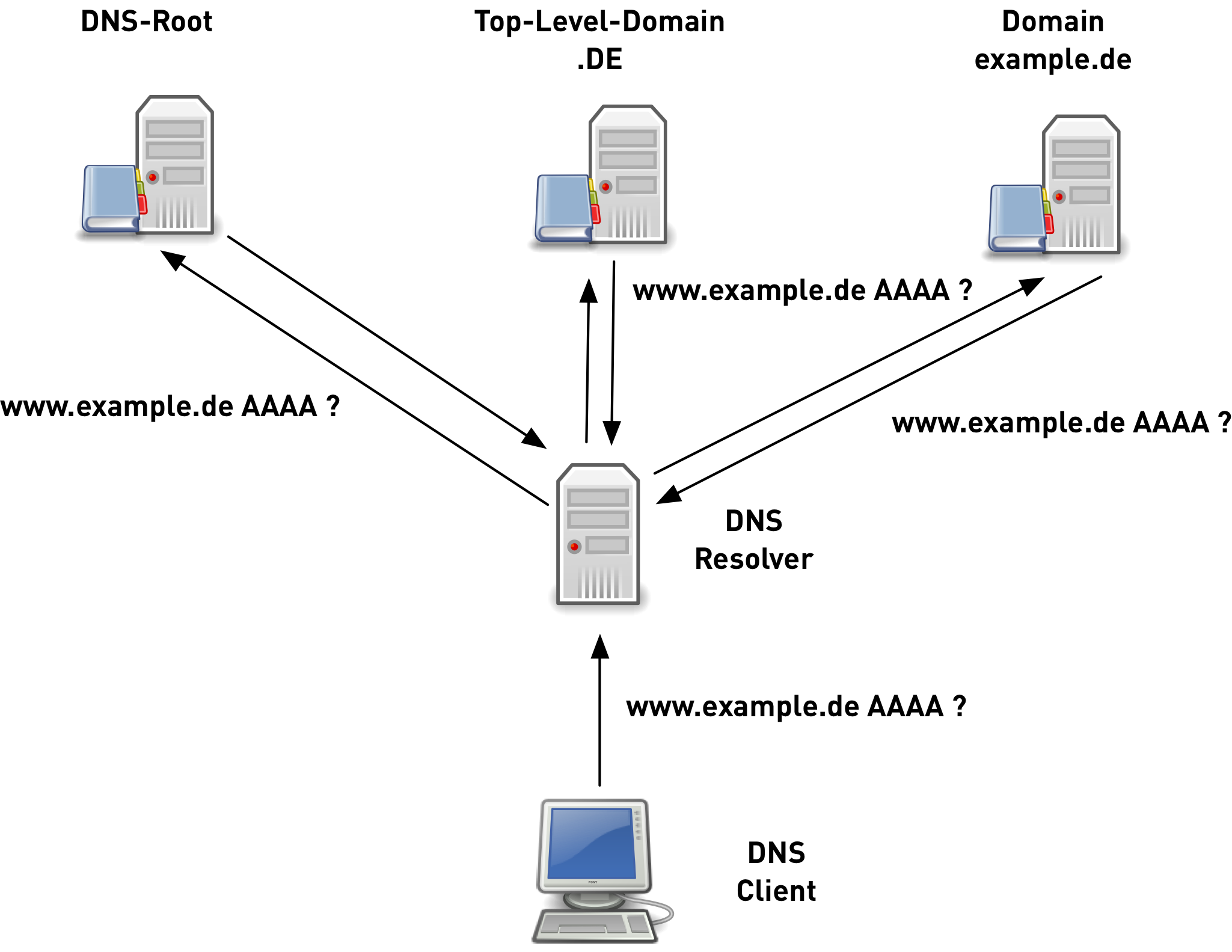
original DNS queries 6/6
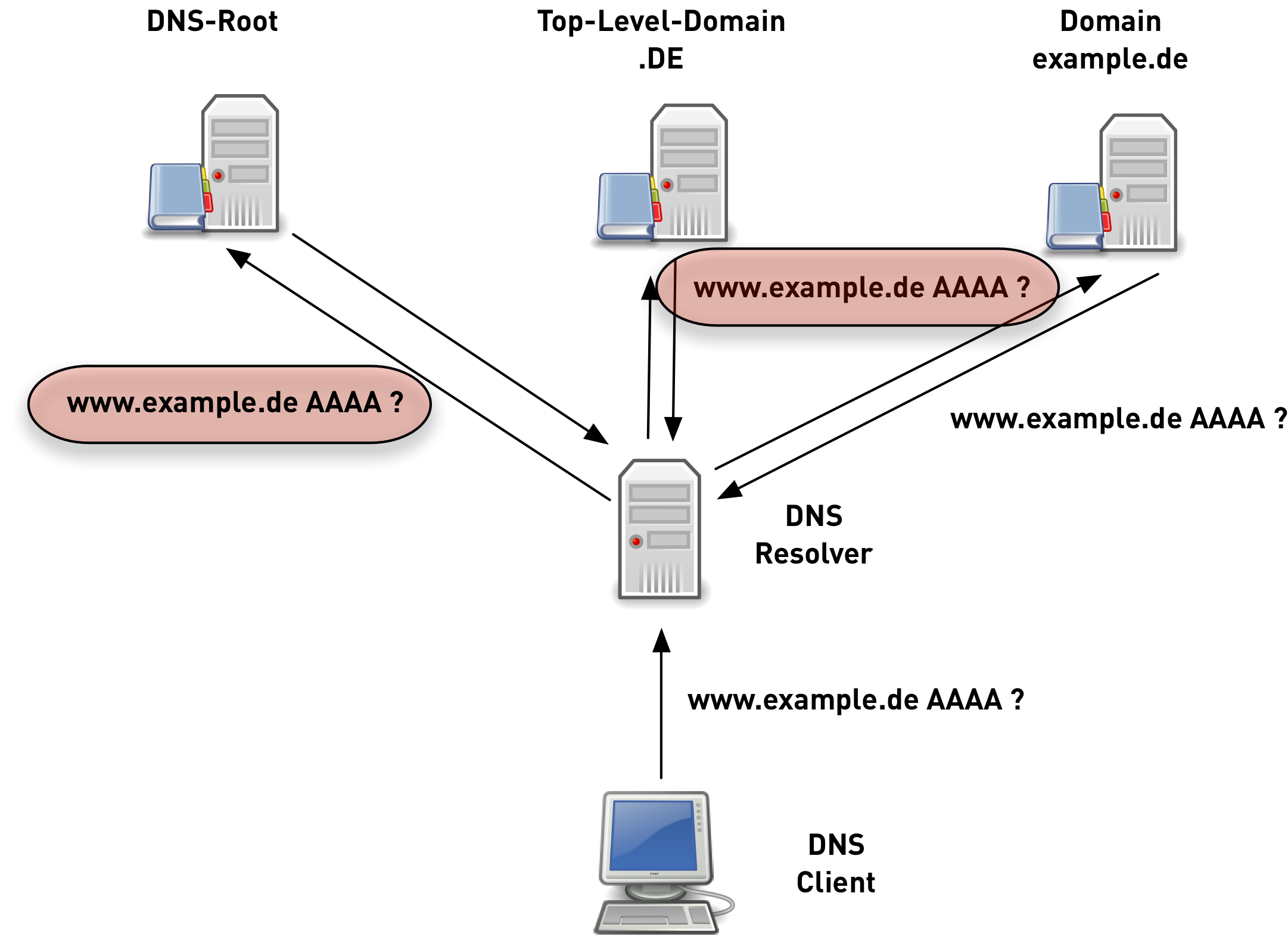
QNAME minimized queries
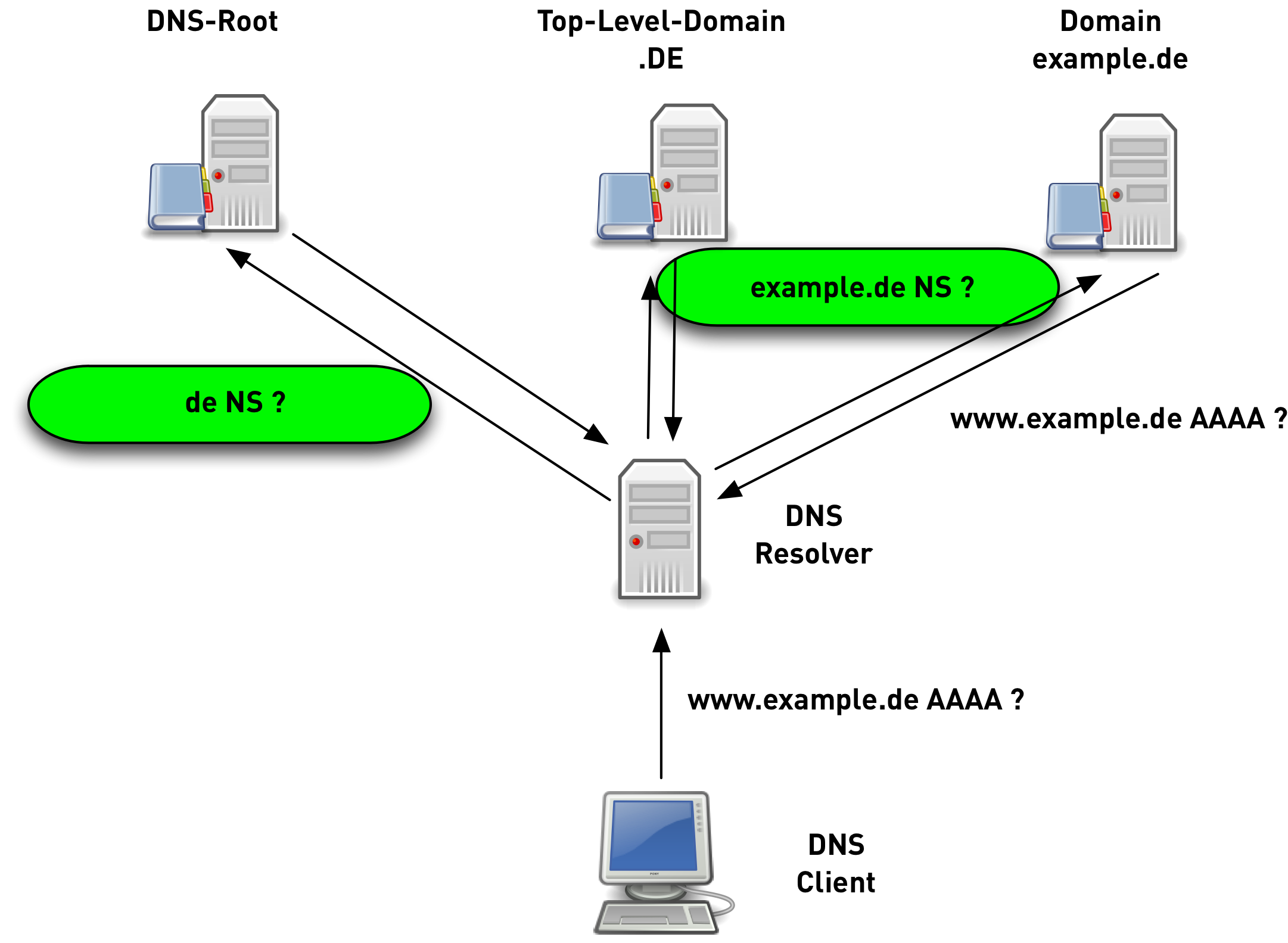
Implementations
- Unbound
- Knot-Resolver
Test
testing if the resolver path supports QNAME minimization
shell$ dig txt qnamemintest.internet.nl +short a.b.qnamemin-test.internet.nl. "HOORAY - QNAME minimisation is enabled on your resolver :)!"
DNS over TLS
- RFC 7858 Specification for DNS over Transport Layer Security (TLS)
- DNS wireformat over TLS over TCP
- Port 853 (TCP)
- encryption and authentication
Performance
- performance of DNS-over-TLS can be quite good
- for existing sessions with TLS 1.3 as good as DNS-over-UDP
- pipelining
- TCP fast open
- 0-RTT resume
- current implementations are not optimized
Implementations
- Client
- Unbound (as local forwarder)
- Stubby (getdnsapi)
- dnsfwd
- Server
- Unbound (as remote resolver)
- Knot
- any DNS server via
stunnel
Developments
- TLS 1.3 deployment stalled because of misbehaving middleboxes (BlueCoat)
- controversial in the IETF, but useful: multiplexing HTTPS and DNS on port 443 (https://gitlab.com/dkg/hddemux)
DNS over DTLS
- RFC 8094 DNS over Datagram Transport Layer Security (DTLS)
- DNS wireformat over TLS over UDP
- Port 853 (UDP)
- encryption and authentication
DNS over DTLS issues
- adversary can block DNS queries
- resource exhaustion attacks against DNS server possible
- no known implementations
DNS over HTTP(S)
- IETF Internet Draft DNS Queries over HTTPS https://tools.ietf.org/html/draft-hoffman-dns-over-https
- DNS HTTP-Format over HTTPS over TCP
- Port 443 (HTTP/2)
- URL: https://server/.well-known/dns-query
- base64url encoded DNS data, Content-Header
application/dns-udpwireformat - encryption and authentication
Benefits
- HTTPS might be the only option in highly firewalled networks
- easy to implement for (Web-)Developers (JavaScript etc)
Additional documents
- Representing DNS Messages in JSON https://tools.ietf.org/html/draft-hoffman-dns-in-json
- DNS Messages in XML (expired) https://tools.ietf.org/html/draft-mohan-dns-query-xml
Similar Implementations
DNS over JSON over HTTPS over TCP
- Google DNS Server-Side
https://developers.google.com/speed/public-dns/docs/dns-over-https
- dingo - A DNS client in Go that supports Google DNS over HTTPS
DNS-Wireformat over HTTPS
- DNS wireformat over HTTP(S) over TCP
- Internet Draft DNS wire-format over HTTP https://tools.ietf.org/html/draft-ietf-dnsop-dns-wireformat-http
- Port 80 or 443 (HTTP 1.1 or HTTP/2)
- URL: https://server/.well-known/dns-wireformat
- Content-Header
application/dns-wireformat - may provide encryption and authentication
- DNS wire-format data is wrapped with a HTTP header and transmitted on port 80 or 443
DNS over QUIC
- DNS over QUIC over UDP
- Specification of DNS over Dedicated QUIC Connections https://tools.ietf.org/html/draft-huitema-quic-dnsoquic
what is QUIC
- modern TCP replacement from Google, now standardized in the IETF
- uses UDP, implements TCP features
- usually implemented in applications, not OS kernel
- includes TLS 1.3
- 0-RTT
- performance in-par with DNS-over-UDP
- QUIC Documents https://tools.ietf.org/wg/quic/
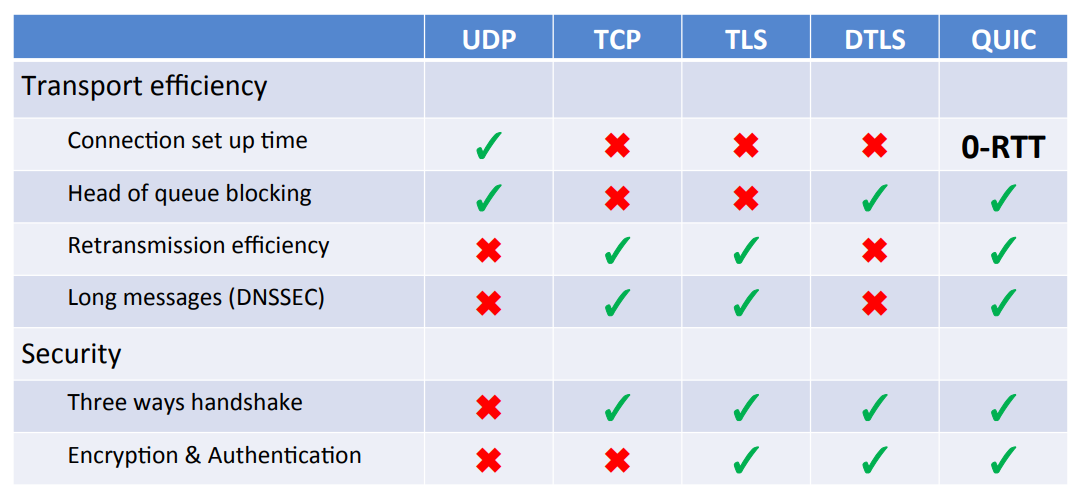
DNS-over-X comparison
DNS over opportunistic IPSec
- DNS over UDP or TCP over IPSec
- DNS queries will be tunneled via IPSec
- provides encryption (but only limited authentication)
- Unauthenticated Opportunistic IPsec https://libreswan.org/wiki/HOWTO:_Unauthenticated_Opportunistic_IPsec
Implementations
- LibreSWAN and Unbound (IPSec Module)
additional work
- make IPSec work in case of heavy firewalling: RFC 8229 TCP Encapsulation of IKE and IPsec Packets
- allows IPSec to work on Port 443 (multiplexed with HTTPS)
DNS over DNSCrypt
- DNS over DNSCrypt over UDP or TCP
- DNSCrypt is a DNS privacy solution originally developed by OpenDNS (now Cisco)
- encryption and authentication
- protocol is open source, but somewhat underdocumented
- client operates a DNS proxy that tunnels DNS over DNSCrypt
- some, but not all DNSCrypt resolver support DNSSEC
DNS over Tor
- DNS over Tor over TCP
- Port 9053
- Tor client proxies the DNS queries through a tor circut
- only A/AAAA-Records supported (no TXT, MX, SOA …)
- no DNSSEC, rogue Tor exit node can spoof DNS traffic
- > 30 % of Tor exit nodes use Google public DNS
Padding of DNS data
- DNS query/responses are small data chunks
- traffic analysis might be acute when dealing with DNS queries
- the IETF is working on padding schemes for DNS to make traffic
analysis more difficult
- RFC 7830 The EDNS(0) Padding Option
- Padding Policy for EDNS(0) https://tools.ietf.org/html/draft-ietf-dprive-padding-policy
Performance
Alexa Top 1000 domains
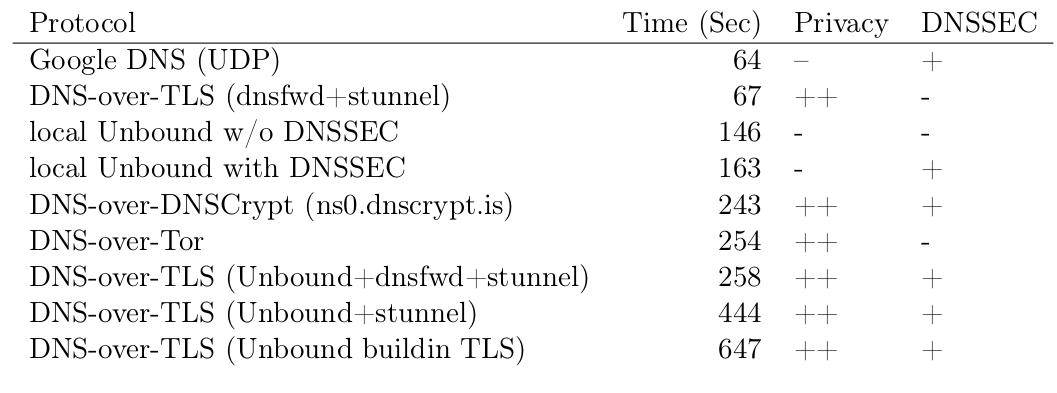
1000 DNS-Queries from office network
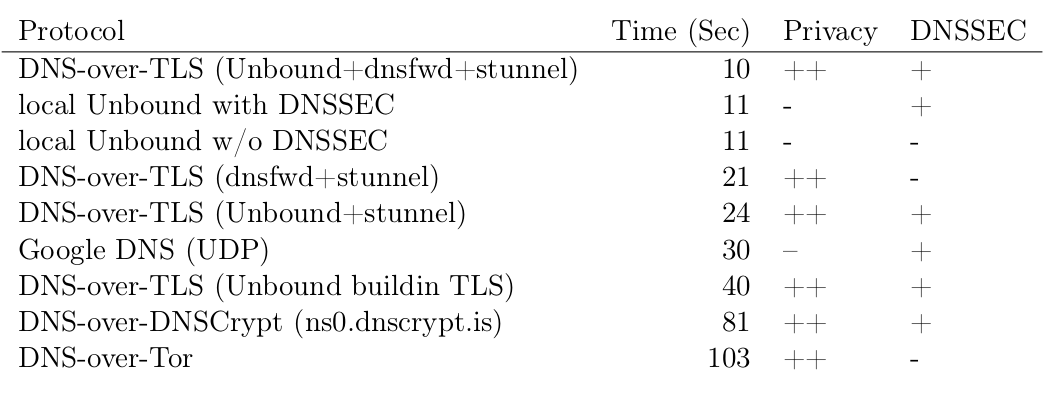
Reading the crystal ball
My totally un-scientific predictions, based on the wisdom of my stomach
- DNS-over-TLS will be implemented, but will have a hard time getting traction
- DNS-over-QUIC will be in Chrome, Opera, Android -> queries towards Google DNS. Fast but not private.
- ISPs (large and small) will loose control over DNS resolution
- good: no DNS interception
- bad: no fast local DNS resolution
- bad: difficult to implement local content caches
- Web-Applications will use DNS-over-HTTPS (but mostly via Google)
Links
Links from this presentation can be found at http://talks.strotmann.de/view/welcome-visitors/view/infosec-stammtisch-ms-dns-over-anything-encrypted